Forescout Secure Connector
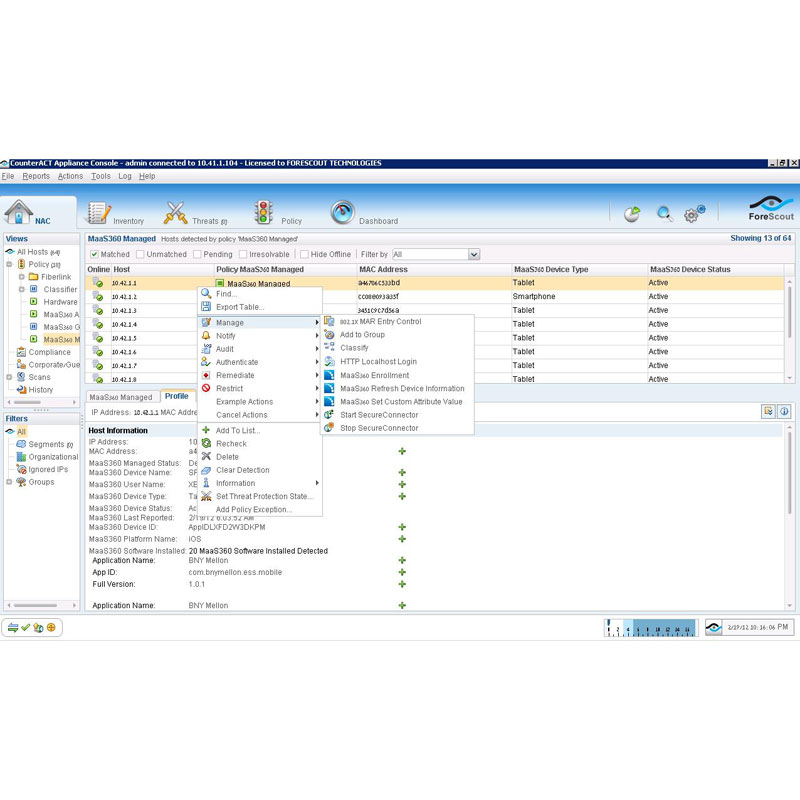
Application: ForeScout CounterACT Secure Connector Operating System tested on: Windows 10 1809 (x64) Vulnerability: ForeScout CounterACT SecureConnector Local Privilege Escalation through Insecure Folder Permissions Overview: This vulnerability exists due to the permissions set on the logs directory used by the ForeScout SecureConnector application. Every several seconds, a new log entry is. Customer has Forescout secureconnector installed on machines for Endpoint Compliance. They are evaluating ISE Posture currently, have a query whether the ISE posture agent can check the compliance status of the secureconnector agent, and then report the machine as compliant/non-compliant. I don't think there is a straightforward way of doing.
Forescout Technologies is proud to offer a Conference Attendee VIP pass.
Forescout Secure Connector Install
Complete the form below to receive a VIP registration code for FREE admission to our next event.
Forescout Secure Connector Download
Connected Devices Are PuttingYour Enterprise at Risk
With over 3,800 customers globally, Forescout actively defends the Enterprise of Things for the world’s leading organizations.
How To Uninstall Forescout Secure Connector
Forescout is the leader in Enterprise of Things security, offering a holistic platform that continuously identifies, segments and enforces compliance of every connected thing across any heterogeneous network. The Forescout platform is the most widely deployed, scalable, enterprise-class solution for agentless device visibility and control. It deploys quickly on your existing infrastructure without requiring agents, upgrades or 802.1X authentication. Fortune 1000 companies and government organizations trust Forescout to reduce the risk of business disruption from security incidents or breaches, ensure and demonstrate security compliance and increase security operations productivity.
Forescout Secure Connector Mac
Don’t just see it. Secure it. Forescout: The Enterprise of Things Secured.